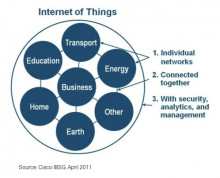
Security industry 'very close' to losing cyber war - WatchGuard
The security industry is "very close" to losing its war against cybercriminals as bugs and malware such as Cryptolocker and Heartbleed threaten to alienate everyday users from the internet.
That is the stark warning of Alex Thurber, vice president of sales at WatchGuard, a 20-year veteran of the security industry.
Talking to CRN yesterday at Infosecurity Europe, Thurber admitted the industry had failed to keep pace with the new breed of threats that have been able to bypass traditional defences. "At some point, we risk losing the everyday user," he said.