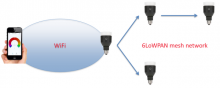
Crypto weakness in smart LED lightbulbs exposes Wi-Fi passwords
In the latest cautionary tale involving the so-called Internet of things, white-hat hackers have devised an attack against network-connected lightbulbs that exposes Wi-Fi passwords to anyone in proximity to one of the LED devices.