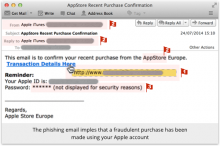
About those alleged backdoors in Microsoft products...
Scott Charney, of Microsoft's Trustworthy Computing, said the government has "never" asked for a backdoor in Microsoft products. Yet a former engineer working on BitLocker claimed the government does ask, but those requests are “informal.”