Configuration errors lead to HealthCare.gov breach
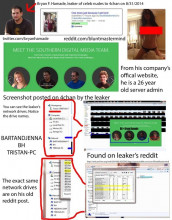
The Health and Human Services Department (HHS) said that HelthCare.gov, the nation's health insurance enrollment website, was breached in July and that the attackers uploaded malware to the server.
The breach, which is the first successful intrusion into the website, was discovered on August 25 by a CMS security team after an anomaly was detected in the security logs of one of the servers on the compromised system.