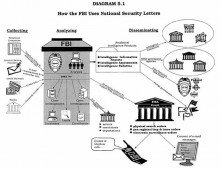
Your Wi-Fi’s WPA2 Encryption Can Be Cracked Offline: Here’s How
When it comes to securing your Wi-Fi network, we always recommend WPA2-PSK encryption. It’s the only really effective way to restrict access to your home Wi-Fi network. But WPA2 encryption can be cracked, too — here’s how.
As usual, this isn’t a guide to cracking someone’s WPA2 encryption. It’s an explanation of how your encryption could be cracked and what you can do to better protect yourself.