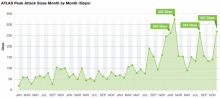
Fancybox WordPress plugin reveals zero day affecting thousands
A WordPress plugin downloaded half a million times has been used in zero day attacks that served up malware.
The plugin in question is called FancyBox and creates a lightbox-like interface with which to look at images. It's been used by unknown actors to deliver a malicious iframe through a persistent cross-site scripting vulnerability identified by Russian researchers Gennady and Konstantin Kovshenin.
The duo provided details to Sucuri chief tech bod Daniel Cid who issued an advisory warning users to dump the plug in.