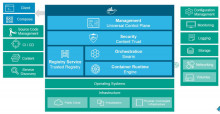
Docker improves container security and management
We love Docker. This container technology makes it possible to run four-to-six times the number of server applications as you can with Virtual Machines (VM) on the same hardware. There are only two little problems: Security and management.
Those aren't small problems. Even though businesses are flocking to deploy Docker containers, if you can't nail down the security or management issues, you're playing with fire. That hasn't stopped anyone, but Docker knows darn well it's only a matter of time before its users get burned. So, Docker is addressing both problems.