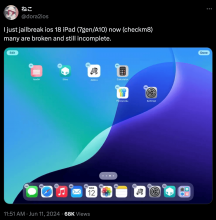
Hackers show off jailbroken checkm8-vulnerable iPad and Apple TV running iPadOS 18 & tvOS 18 respectively
A lot of people are wondering if we’ll ever see a jailbreak for iOS & iPadOS 18, and while we don’t have a crystal ball clear enough to give you a definitive answer, we will say that there’s at least a chance the iPad (7th generation) gets a jailbreak thanks to being susceptible to the checkm8 hardware-based bootrom exploit and being compatible with iPadOS 18 – the last checkm8-vulnerable iPhone or iPad meeting both of those criteria.