JTAG Hacking An SSD With A Pi: A Primer
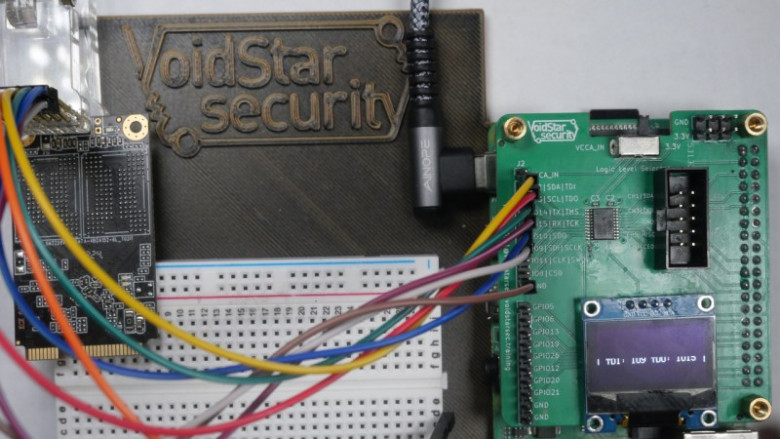
[Matthew “wrongbaud” Alt] is well known around these parts for his hardware hacking and reverse-engineering lessons, and today he’s bringing us a JTAG hacking primer that demoes some cool new hardware — the PiFEX (Pi Interface Explorer). Ever wondered about those testpoint arrays on mSATA and M.2 SSDs? This write-up lays bare the secrets of such an SSD, using a Pi 4, PiFEX, OpenOCD and a good few open-source tools for JTAG probing that you can easily use yourself.
The PiFEX hat gives you level-shifted bidirectional GPIO connectors for UART, SPI, I2C, JTAG, SWD and potentially way more, an OLED screen to show any debugging information you might need, and even a logic analyzer header so that you can check up on your reverse-engineering progress.
The suggested software workflow pulls no punches either, proposing ease-of-use features like USB-Ethernet gadget mode and Jupyter notebooks. [wrongbaud] shows us how to find JTAG among the dozen testpads left on the SSD, get the SSD single-stepping through code, and dump some of its memory space as a test. Full of tricks of the trade like reverse-engineering devices on a sheet of paper you can leave markings on, this write-up gives you a solid background in JTAG hacking, even if you only have a Pi and an old SSD.









































































