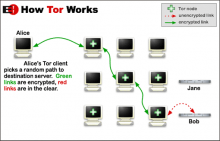
Here’s What Tor’s Data Looks Like as It Flows Around the World
For a tool that’s meant to serve as a cloak of online anonymity, Tor is surprisingly transparent. The non-profit Tor project whose software powers its network of thousands of volunteer proxy computers also publishes a frequently updated collection of data about the location and bandwidth of those privacy-enhancing machines on desks and in datacenters around the world. Now a data visualization company has assembled that data into an interactive graphic, beautifully capturing the Tor network’s complexity and scale.